
350 Revere Beach Blvd , PH 11G
Revere, MA 02151
Listed By CENTURY 21 North East

350 Revere Beach Blvd , PH 11G
Revere, MA 02151
Listed By CENTURY 21 North East

17 Davis St
Revere, MA 02151
Listed By CENTURY 21 North East

41 South Ave
Revere, MA 02151
Listed By CENTURY 21 North East

26 Arlington
Revere, MA 02151
Courtesy Of Keller Williams Realty Evolution

109 Salem St , 405
Revere, MA 02151
Listed By CENTURY 21 North East

23 Avon Street
Revere, MA 02151
Listed By CENTURY 21 Mario Real Estate

4 Belle Isle Ave
Revere, MA 02151
Listed By CENTURY 21 North East

300 Fenno St 20
Revere, MA 02151
Courtesy Of Keller Williams Realty Chestnut Hill

15 Richie Rd
Revere, MA 02151
Listed By CENTURY 21 North East

42 Madison St
Revere, MA 02151
Courtesy Of RE/MAX ANDREW REALTY SERVICES

48 Kilburn St
Revere, MA 02151
Courtesy Of Keller Williams Realty Chestnut Hill

88 Malden St
Revere, MA 02151
Listed By CENTURY 21 North East

175 Ward 46
Revere, MA 02151
Courtesy Of Keller Williams Realty Evolution

65 Alden Ave
Revere, MA 02151
Listed By CENTURY 21 North East

1133 N Shore Rd , 201
Revere, MA 02151
Listed By CENTURY 21 North East

521 Proctor Ave
Revere, MA 02151
Listed By CENTURY 21 North East

45 Mccoba St 70
Revere, MA 02151
Courtesy Of Keller Williams Realty Evolution

156 Salem Street
Revere, MA 02151
Listed By CENTURY 21 North East

31 Hillside Ave , 1
Revere, MA 02151
Listed By CENTURY 21 North East

52 Crest Ave
Revere, MA 02151
Listed By CENTURY 21 North East

41 Oak Island St
Revere, MA 02151
Courtesy Of Keller Williams Realty Success

350 Revere Beach Blvd , 12P
Revere, MA 02151
Listed By CENTURY 21 North East
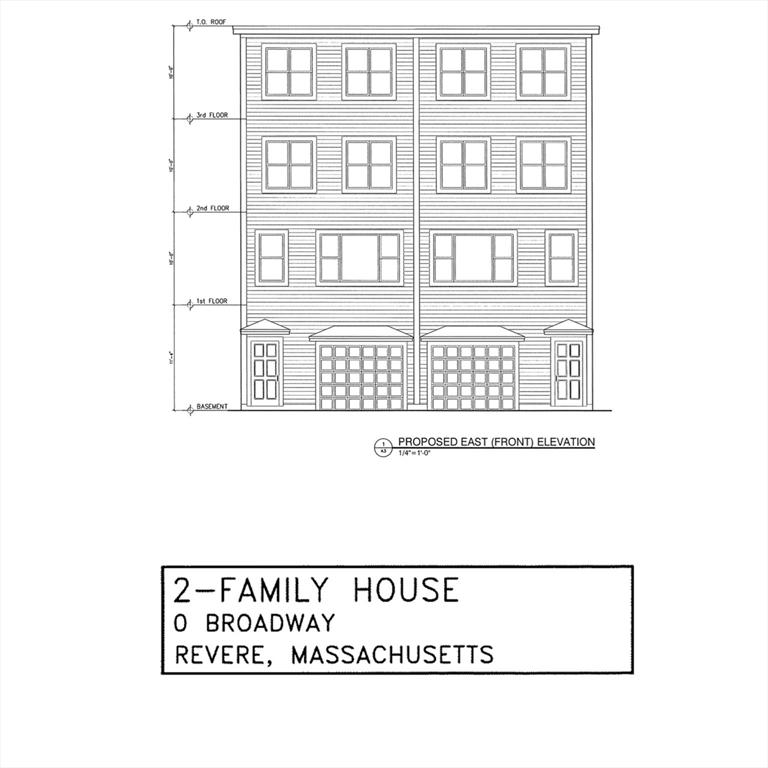
0 Broadway (lot 68)
Revere, MA 02151
Listed By CENTURY 21 North East

21 Bellevue Ave. , 1
Revere, MA 02151
Listed By CENTURY 21 North East